Nearly five million attacks against desktops at home in the Philippines were recorded from January to June this year, according to a cybersecurity firm.
Kaspersky released this report as work-from-home setups continued to persist due to the still raging COVID-19 pandemic in the country.
The firm found a total of 4,877,645 attempted attacks against users or customers of Kaspersky in the Philippines from January to June 2021.
This is 98.41% higher that translates to 2,458,364 attacks from the same period in 2020.
Here’s a table of comparison of the attacks recorded during the same period in 2020 and then in 2021:
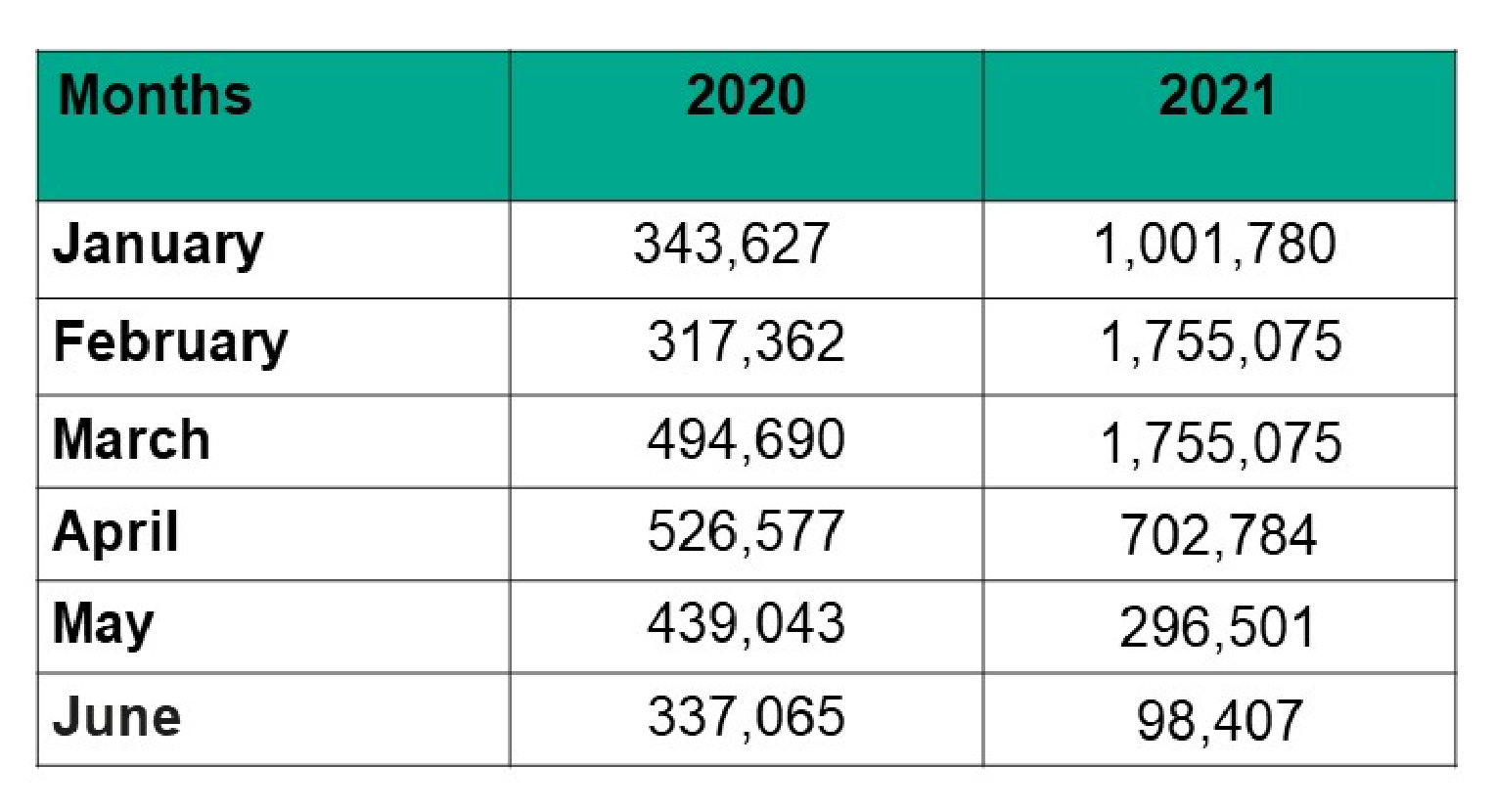
Based on the data, the highest attacks were detected in February and March with 1,755,075 for both months.
Kaspersky stated that the type of attacks they monitored is called a brute-force attack.
They defined a brute-force attack as “a way to guess a password or encryption key by systematically trying all possible combinations of characters until the correct one is found.”
These attacks were assessed among laptops installed with Microsoft’s propriety protocol called Remote Desktop Protocol (RDP), the study stated.
Kaspersky noted that Microsoft remained the most installed operating system among Filipinos.
“These have been the devices heavily relied upon by employees working remotely while Metro Manila and other key provincial cities were put into on and off lockdowns since the pandemic began,” Kaspersky noted.
According to the report, the RDP is “Microsoft’s proprietary protocol (set of rules or procedures for transmitting data between computers through a network) used to control servers and remotely connect to other computers running Windows.”
“A brute-force RDP attack targets a device running Windows (definitely using RDP) and tries to find a valid RDP login or password pair. If successful, it allows an attacker to gain remote access to the targeted host computer,” it said.
Kaspersky researchers stated that the cybercriminal activities had skyrocketed since March 2020, which is also the same month when the tough lockdowns were first implemented.
They cited that the attacks mostly target “corporate resources” that hastily made the transition from office work to remote work across the world.
Yeo Siang Tiong, general manager for Southeast Asia at Kaspersky, emphasized this in a statement.
“The hurried mass transition to home working has given cyber attackers this logical conclusion that poorly configured RDP servers would surge and then we saw the number of attacks shoot up tremendously,” Tiong said.
Recommendations to employers
Companies and businesses should therefore ensure security in their work-from-home arrangements moving forward.
“Now that remote work is projected to be the next step as the future of business evolves, it would be to every company’s advantage to pay attention to establishing and improving their cybersecurity policies,” Tiong said.
“Attacks on remote-access infrastructure, including collaboration tools, are unlikely to stop any time soon so we call on businesses and employees to look into securing their work-from-home set-up better,” he added.
The cybersecurity firm recommended the following protective measures to companies whose remote workforce are using RDP:
- Use strong passwords.
- Make RDP available only through a corporate VPN.
- Use Network Level Authentication (NLA).
- Enable two-factor authentication, if possible.
- Disable RDP if not using it and close port 3389.
- Use a reliable security solution.










